In many cases, security comes at the expense of productivity. It is important and necessary to secure sensitive data, as this keeps the information safe and limits risk exposure, especially when this information is stored and shared across the organization. To make the most of this information it needs to be shared quickly and easily.
The tension exists because often there is a productivity “toll” taken by security requirements that could also be achieved in another less disruptive way. In this blog post, we will discuss the dichotomy between security and productivity and show how Satori’s Data Security Platform can provide security that actually increases productivity.
A good example of the tension between security and productivity is Two Factor Authentication (2FA).
Example - Two-Factor Authentication
A two-factor authentication mechanism asks the authenticating user for additional detail, to lower the risk of their (usually) password being compromised resulting in a breach. By requesting, for example, a temporary token, we can prevent authentication even if a password is compromised. However, this added layer of security comes at the expense of productivity, as it takes more time to log into the system, as well as the time lost for setting up 2FA and maintaining any changes. In most cases, the productivity loss will be relatively small compared to the reduced risk.
When It Comes to Data Access…
Data is a productive resource in many organizations, but in particular B2B organizations. These organizations manage customer information that contains sensitive PII and PHI data. In order to maximize productivity and profitability organizations rely on the quick and scalable movement of data. However, since this data contains sensitive information and is often subject to compliance regulations from GDPR and HIPAA, and in order to lower exposure risk there must be controlled access to data.
Data access is often either based on roles (RBAC), attributes (ABAC), policies, or some combination of these. Regardless of the type of access control the necessity of granting, and just as importantly revoking, access depends on data engineering teams. Engineering teams must work through the cumbersome process of having to manually go through all of the support tickets to grant access. Often costing the data engineering teams precious resources, including time and productivity; in addition to manually setting up data security policies to enforce the protection of customer data. Over two-thirds of our State of Data SecOps Report respondents indicated that they use manual error-prone processes to grant access. This reliance on engineering teams can result in over-granting privileges and persistent access that is not up to date. The danger with over-privileged users is exposure to increased data security risk.
To learn more read about how Access Control is the Dementor of Data Engineering team.
Which Is Why We Decided To Do It Differently…
We believe that the greater the productivity toll on users, the more they will try to circumvent and find alternative ways around the controls. In the case of data access, when faced with mounting bureaucracy, users develop alternative “shadow data access” paths around security controls. Either that, or they will simply lose a lot of data-driven value as they’re frustrated by the security controls.
We have heard from data teams that they will often just grant blanket access to avoid having to deal with the overwhelming number of support tickets. In these cases they can even adopt an “I don’t want to know about it” approach, taking the chance they won’t be exposed during a security incident or caught by compliance and risk regulators.
We built Satori with this in mind, as our philosophy is to make security the simple and productive choice for data-driven organizations. That’s true from the initial implementation to day-to-day work with Satori.
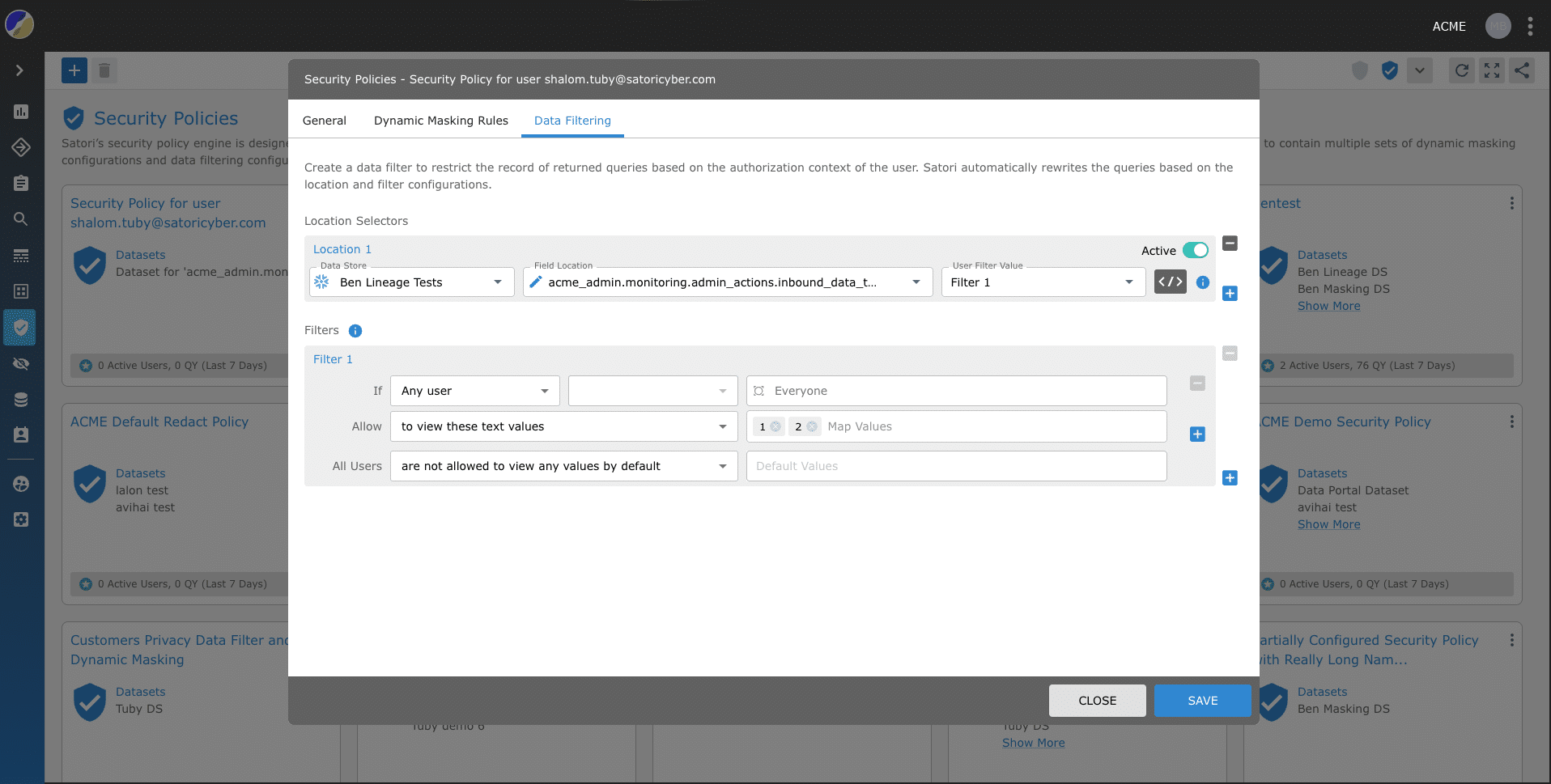
1. Security Policies
It was important for us to design our security policies engine so that it does not pose limitations for users due to the underlying data platforms being accessed and their specific capabilities. We created a security policies engine that is a productivity enabler, as it is easy to translate business logic (for example: “you will get all customer data anonymized”) to a technical working security policy. Thus, these policies can be applied by security teams and data owners, not only data engineers in minutes reducing the drain on productive resources.
2. Data Access Enablement
In the same way, it was important for us to allow companies to manage access to data with as little productivity loss as possible. This means moving from persistent controls to setting temporary “just in time” (JIT) data access in the simplest way possible. The application of JIT access control applies to both RBAC and ABAC regardless of the underlying data technology and where the data is stored.
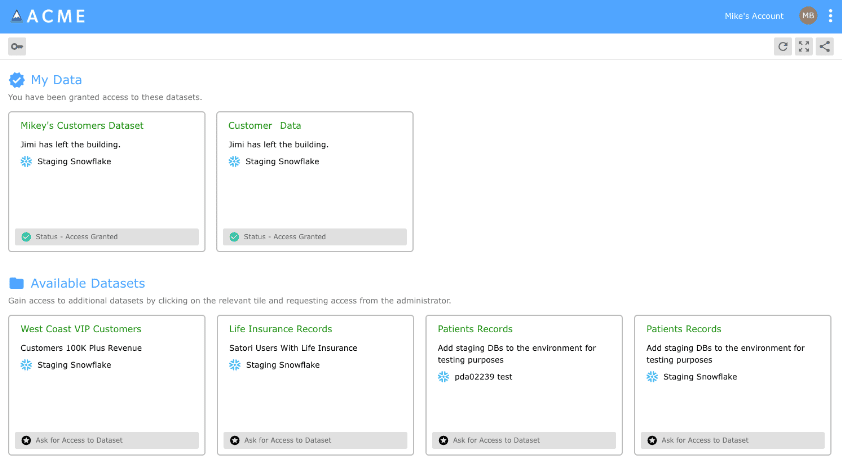
3. Data Portal
The data portal enables data users within companies to “shop” for available datasets and get immediate access to the datasets presented, across all data platforms. This accelerates productivity of data users, as they would otherwise have to wait days or even weeks before gaining access.
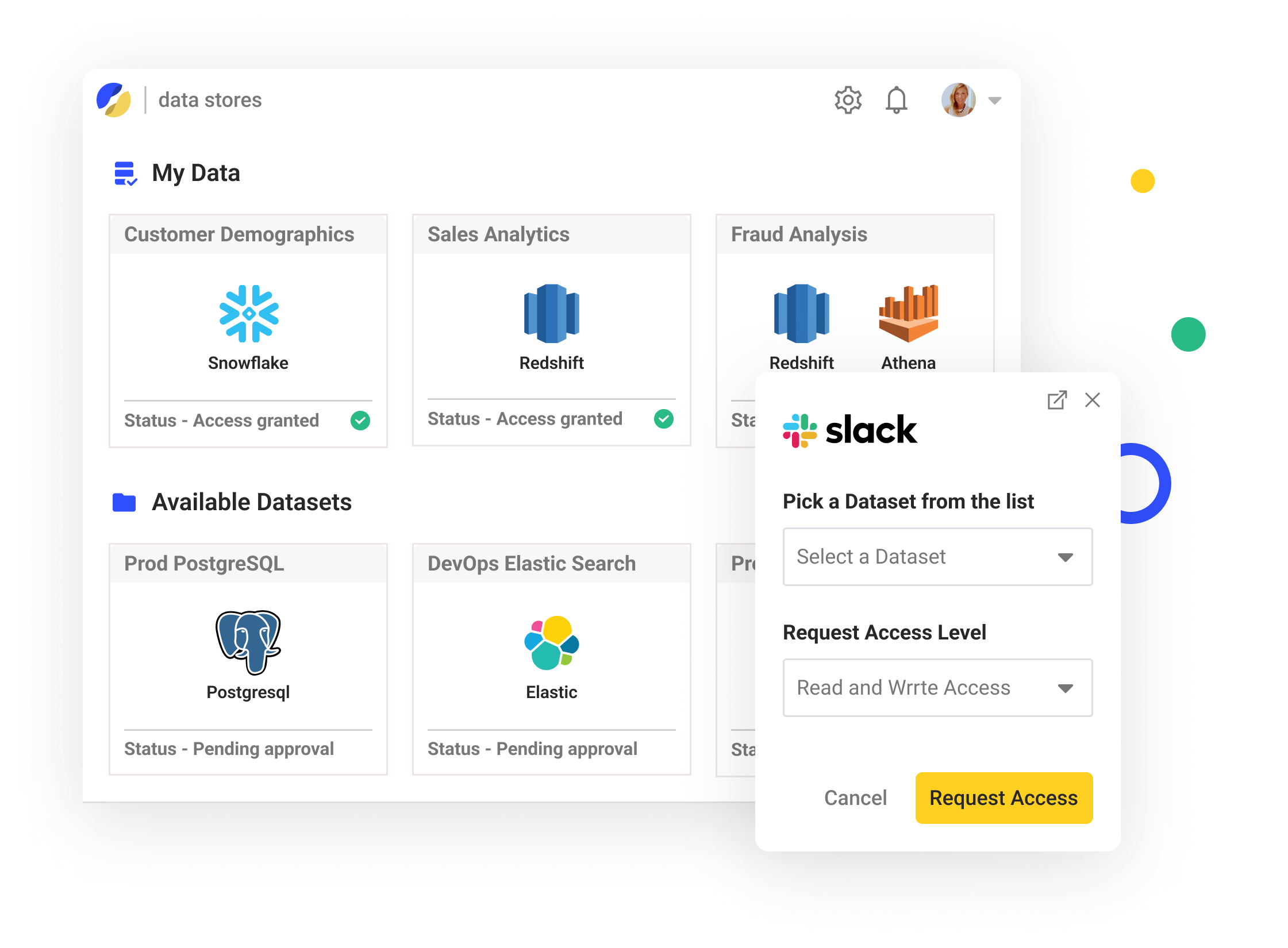
4. Slack Integration
We further streamlined the process improving productivity by integrating the data portal with slack and other platforms. Data consumers can now use their already existing platforms to gain access to data, without having to learn and integrate another different platform.
Conclusion
Satori helps you to have your cake and eat it too. Using Satori’s Data Security Platform means that security does not have to come at the expense of productivity. Instead, access control can be simplified and streamlined using access control tools such as the self-service data access controller (including Slack integration), just-in-time access controls and the data portal. Altogether saving time and resources for the data-engineering team and allowing data to move quickly and easily across the organization.
Learn more about our access control management or book a demo with one of our experts.




