With so many productivity and enterprise applications online, there’s no shortage of ways to build a toolbox for your business. But even with all these options, it may be difficult to find the tools that are just right for what you need. Luckily, there’s an app for that.
Retool is a fantastic resource for businesses to develop and build their own apps and other useful digital tools. Instead of relying on pre-made dashboards, admin panels, apps, and other solutions, you can build these tools yourself using a drag-and-drop interface that’s easy to use and quick to implement.
One of the most powerful features Retool has to offer is its ability to integrate seamlessly with other apps and databases including Slack, Stripe, Twilio, MySQL, PostgreSQL, and Redis, among others.
With users able to access your Retool web apps from either side of your business – whether they’re employees or customers – a big question remains: how do you keep your Retool apps secure?
In this article, we’ll explore Retool and how it can be used, some common security risks to consider, as well as some best practices to keep your apps and the databases they’re integrated with safe.
What is Retool?
The answer is simple: it’s an app to quickly build other apps and tools. Retool connects directly to data sources and then provides a wide variety of features for its users.
Instead of building an app completely from scratch, Retool enables developers to build interfaces by dragging and dropping various components and elements. Not only does this save companies and programmers time, but it also allows its users to create customized solutions rather than picking and choosing pre-made tools and hoping they integrate well.
While app builders are often limited by the components available, developers can create their own custom components that will slot into Retool-made apps. Leveraging JavaScript, wrapped expressions, and transformers, if Retool doesn’t already have the component you’re looking for, you are equipped with the tools to make it yourself.
Why is Access Control A Concern with Retool?
Retool connects directly with the databases. Therefore organizations implementing a Retool app allow users to access data, which may include sensitive PII data.
However, this data access is aggregated to the database user level. Once a user accesses the data, the database access log contains a generic user, instead of the actual user connecting to the database.
- For example: if the user ‘Mike’ connected using a Retool app configured using the ‘app_retool’ user, the database access log will have ‘app_retool’ as the user, rather than the actual user (Mike).
- Another example is the type of data being accessed by individuals: with the same user one individual could have accessed email addresses while a different individual only looked at the audit logs. In many cases, different access policies should be applied depending on these users’ roles. For example, Mike from accounting can see all customer data in clear text, while Anna, a data analyst, should only be able to access anonymized customer data.
This is an important distinction for two reasons. First, in order to remain secure and compliant organizations need to know who is accessing what information. Second, providing too much access, or over privileged access, to users can result in data exposure whether intentional or not.
So while the Retool user interface is more user-friendly for non-technical staff; this could result in uncontrolled access to sensitive data.
How Satori Ensures Data Security with Retool
The Satori Data Security Platform allows organizations to use Retool to meet security and compliance requirements in a simple way. We outline these below:
- Just-in-time access controls. Satori enables organizations to set access controls simply and easily. This access can be on a need-to-know basis and revoked after a specified period of time. This ensures that users are not over privileged.
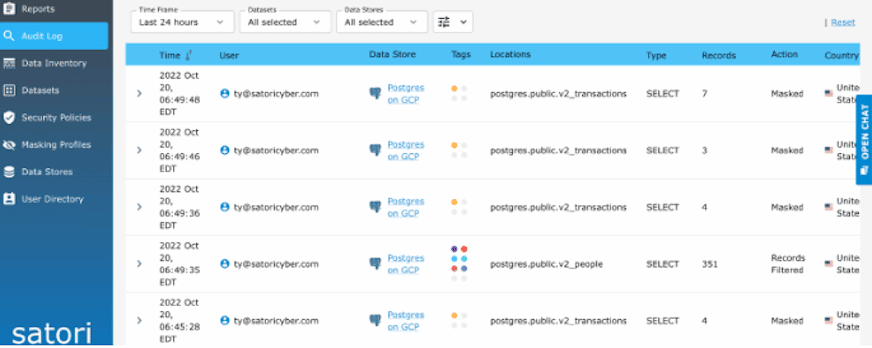
- Detailed auditing and monitoring. Satori provides detailed information about who has been accessing information within the database. If a single user name is used to access data through Retool, Satori tracks and logs all of that individual’s activity. This auditing and monitoring feature provides the security and compliance teams with the information they need to ensure that only those with the correct authorizations access data; ensuring the organization exceeds security and compliance regulations.
- Applying security policies on data access. Security policies can easily be applied to data access using Retool. This includes dynamic data masking (where data is anonymized according to the user or their roles), RBAC, ABAC, and row-level security.
An Example of How Satori Secures Email Addresses with Retool
1. In retool.com, connect to your Satori endpoint using the appropriate credentials or service account.
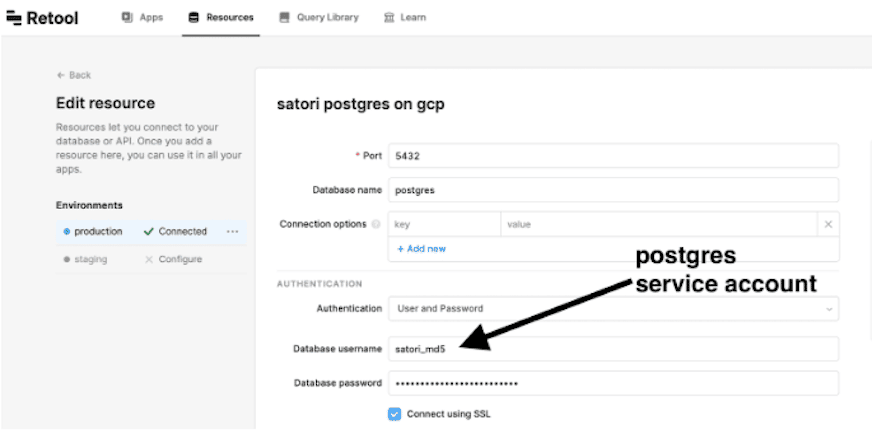
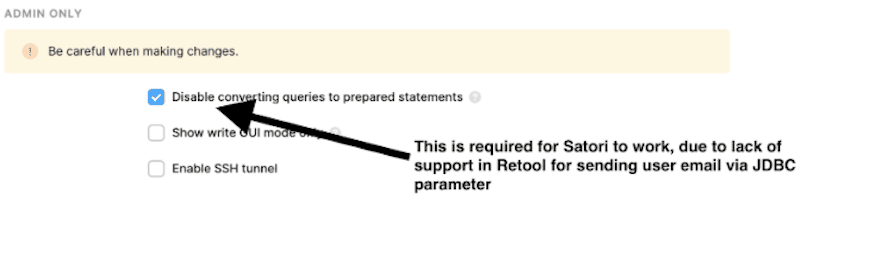
Important: scroll down to the bottom of the connection screen and check the box for Disable converting queries to prepared statements. This is required for the Retool/Satori experience:
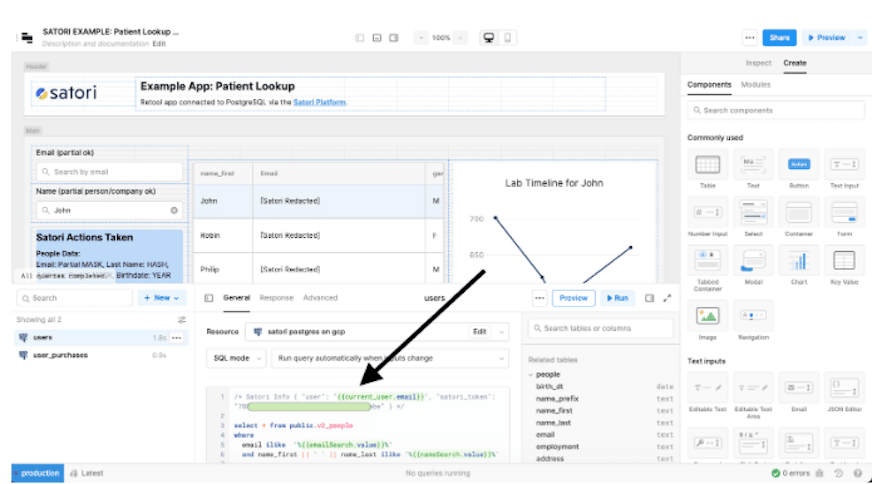
2. To separate individual users you can configure the access so that it sends the email as a comment in each query and the token to validate so that you know exactly who has accessed which data.
On your Retool application, change the SQL for all of your connections, adding a special comment to the beginning of each statement:

If you hover over the text {{current_user.email}} with your mouse, you will notice that Retool correctly and dynamically looks up the user info:
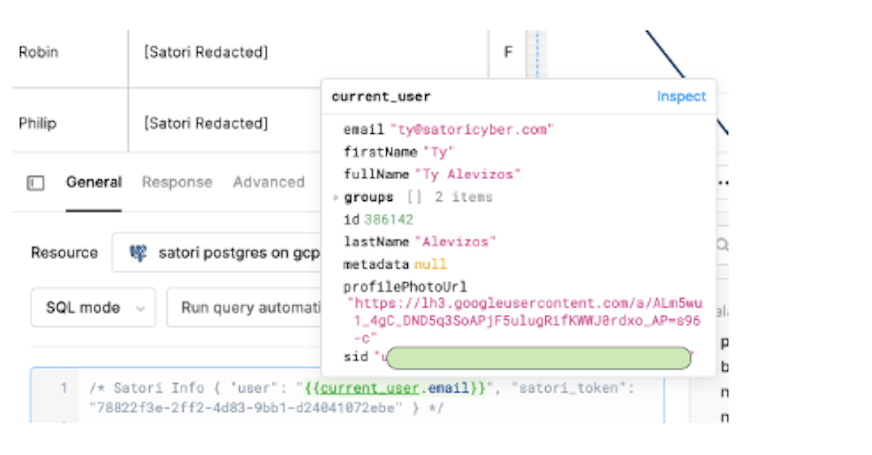
This helps prove that you have configured everything correctly.
Now anytime a user runs a retool application with the above configuration, the true end user’s email/login will be correctly logged inside of Satori:
Ease of use
Connecting the Satori Data Security Platform with Retool enables you to gain control over access, receive detailed audit reports, implement just-in-time access controls, and provide row-level security.
To learn more about Satori:




