As sad as it is, someone has to say it: in most companies, access to data is given on a permanent basis (or almost), for no good reason. Users who need access to data for a specific amount of time, or for the scope of a project, get it for life – or at least long after it’s no longer needed.
Access to data, especially sensitive data, is a critical layer within your company’s security infrastructure. User authentication is just one of these layers, albeit an important one.
Temporary authentication and the use of just-in-time access controls limit the ability of users to access data, including production data, define the period of time they are able to access data, and then revoke access. Temporary authentication enables quick access to data while also ensuring that access is only granted for a specified period of time.
In this blog, we explore temporary authentication and why it’s a necessary component in a comprehensive data security platform.
What is Authentication?
Authentication – whether it relates to logging into a database, accessing a website, or anything where two machines communicate over a network – is a digital handshake. It’s the process of the client (the machine attempting to access something) verifying their identity to the host server (the machine receiving the access request). Practically, authentication occurs through the verification of credentials, using key-pair authentication, or a SSO (single-sign on) with an IdP (identity provider).
Why is Authentication Important?
Organizations collect a large amount of data, often this includes sensitive PII or PHI data that is spread across data warehouses, lakes, or bases. Organizations gain value with this data by sharing data quickly across different users. However, not all users require or should have access to the sensitive information within this data. Authentication is necessary to ensure to that only those individuals who should have access to sensitive data have access to this data and for a specific period of time. Authentication is a necessary component for data security.
Authentication is often required to meet specific compliance requirements. Data regulations such as GDPR and HIPAA, require in most cases some form of user authentication. Failure to have this available authentication can lead to failed audits, delays in processes or higher overhead costs.
Temporary Authentication vs. Permanent Authentication
There are two forms of authentication: permanent and temporary. Permanent authentication keeps a user authenticated throughout their session or, in some cases, even beyond that (think of the “Remember me” features of your favorite websites when you log in on a new machine).
Temporary authentication is limited in time (canceled after a specific period of time, or a particular period of idle time). This kind of authentication is standard for various institutions that handle sensitive data, including banks and government entities. It is necessary to ensure that employees who don’t need or shouldn’t have permanent access to sensitive information only have access to the information that they require for a specific period of time.
DevOps and data engineers who are overwhelmed with granting access tickets can also find it almost impossible to revoke access. Granting blanket access or access that isn’t revoked can present a significant security risk to the company (See: Principle of Least Privilege). Temporary authentication significantly reduces this security risk by revoking access to data at the end of the specified period of time.
Read more Access Control is the Dementor of Data Engineering Teams.
While permanent authentication provides convenience for the end user, as users prefer to not have to go through the approval process, temporary authentication is much safer for both the user and the database they’re accessing.
Temporary Authentication for All Your Data With Satori
Temporary authentication is important for security, productivity, and compliance. Satori’s temporary authentication through automated data access simplifies the process of managing users on databases or configuring SSO with your IdP and cloud providers.
Just-In-Time Access
Satori’s just-in-time (JIT) data access provides temporary access to data. The application of JIT access control applies to both RBAC and ABAC regardless of the underlying data technology and where the data is stored. Temporary access and authentication enable users to quickly gain access to data for a specified period of time.
Automating access to data increases the productivity of data engineers, admins, and users; improves the security of your data; and helps you to meet security and compliance requirements.
Self-Service Access to Data
Satori provides temporary authentication through a self-service access controller (including integrations with Slack and Jira). Data owners and security teams set automated access policies, so that access to data is simplified and occurs in just minutes. This temporary automated access means that there are no lengthy lines for gaining access reducing the likelihood that users will share a single sign-on.
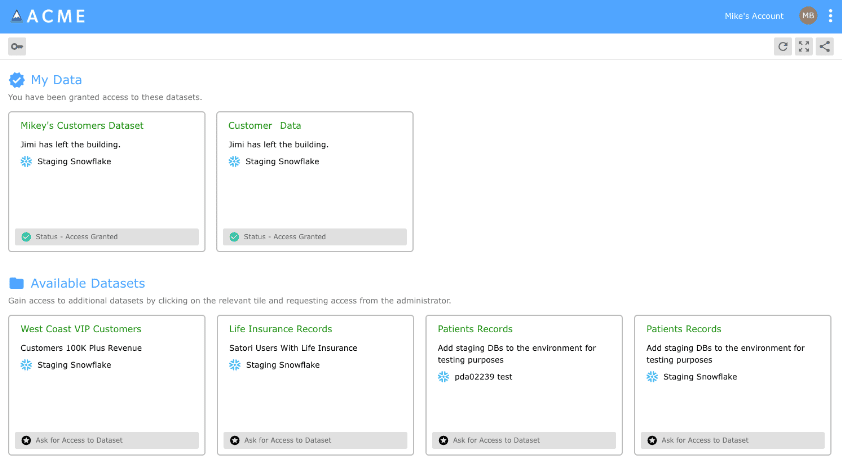
Data Portal
Using Satori’s data portal you have the ability to determine what datasets are available and get immediate access through the use of temporary credentials. This use of consistent temporary access across multiple databases, warehouses, and lakes improves data security and productivity.
Read more about how to configure the data portal for temporary authentication.
Conclusion
Satori, the data security platform enhances security, productivity, and compliance through the use of temporary authentication. With Satori JIT, self-service data access, and the data portal provide the option to gain access to data on a need-to-know basis at scale.
To learn more about temporary authentication with Satori:
- Book a demo with one of our experts
- Video: Satori’s Data Portal
- Self-Service Access To Data




