Proactive and reactive data security are both crucial components of any comprehensive cybersecurity strategy. Proactive security measures involve identifying and mitigating potential threats before they cause harm. On the other hand, reactive security measures are actions taken in response to a security breach or threat after it has occurred. Together, these strategies work to protect sensitive data and other IT resources from unauthorized access.
In this post we explore the different approaches to data security and how to ensure that your sensitive data is protected.
Key Differences Between Reactive and Proactive Data Security
Reactive data security is an approach that focuses on responding to security breaches after they have occurred. This may involve measures such as incident response, disaster recovery, and forensic analysis. While reactive security can be effective in managing breaches, its main drawback is that damage has already been done by the time actions are taken.
For its part, proactive data security takes a more forward-thinking approach as it seeks to prevent breaches from occurring in the first place. This approach involves measures like data loss prevention (DLP), penetration testing, data access control, posture management, and automation.
Put this way, it would be logical to think that organizations would give priority to adopting a proactive data security approach. Unfortunately, this is not the case.
According to CPO magazine, 65% of board members feel that their organization is at risk of a material cyber attack in the next 12 months.
That said, it’s worth digging deeper into the proactive measures your business can start to implement to avoid being part of the statistic.
Data Access Control: Self-Service and Just-In-Time
Data Access Control, a key element of proactive data security, includes two primary approaches: Self-Service and Just-In-Time access control.
Self-Service Data Access
Self-service access empowers users through a personal data portal to manage their access rights, reducing the workload on IT departments.
For instance, an employee can view all available data from a personal data portal.
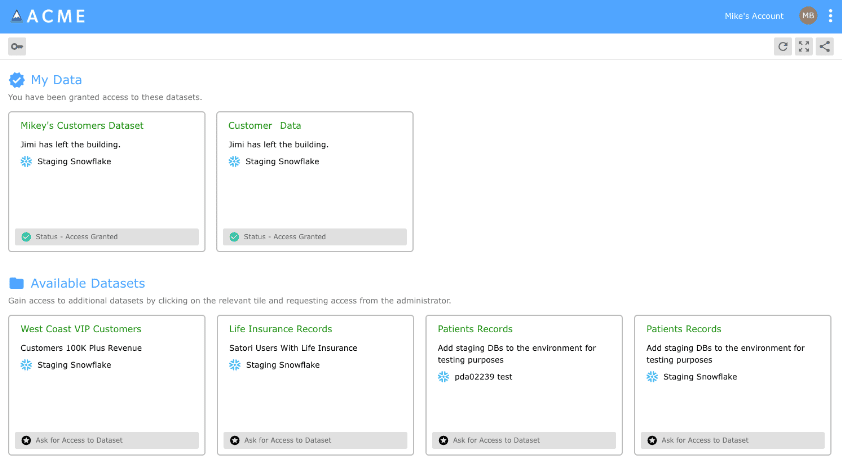
They can then request access to specific data or applications required for their role and receive approval in seconds.

This approach enables organizations to share data more quickly and easily across the organization, improving the time-to-value from data and enhancing productivity and innovation.
Just-In-Time Data Access
Just-In-Time (JIT) access control is also a proactive data security solution. JIT provides access rights for a limited duration, just when it’s needed. For example, a senior staff member may be granted JIT access to review sensitive data, after which those rights would be revoked. This minimizes the risk of unauthorized access or insider threats. JIT is preferable in situations requiring high-security levels or where access to confidential data is needed infrequently.
Both methods have their merits, and the choice depends on the organization’s culture, trust level, and security requirements. That’s why implementing a combination of both can often provide an optimal balance between security and flexibility.
Posture Management in Proactive Data Security
Posture management, another essential aspect of proactive data security, involves assessing and managing your organization’s security stance to reduce cyber vulnerabilities. By adopting an attacker’s mindset, posture management allows for the identification of potential weak points before they are exploited.
This approach is akin to a self-inflicted stress test, providing a proactive rather than reactive means of safeguarding data. Identifying critical roles within the system is another aspect of posture management; since knowing which roles have access to sensitive data can help develop targeted security measures.

Finally, testing incident response is also essential in posture management. By simulating cybersecurity incidents, your organization is testing the resilience of the system and the effectiveness of your team’s response. Thus, posture management acts as a vital shield, strengthening your data security infrastructure against potential threats.
Proactive Data Security is trending towards automation
You can think of automation as the perfect tool to take proactive data security measures to the next level.
For example, by automating repetitive tasks, organizations can reduce human error, a common source of security breaches. This applies to numerous scenarios, such as automated security patches, revoking privileges if a user is inactive for a certain amount of time, or scanning for open ports.
A proactive stance, coupled with automation, could revolutionize how we manage data security, turning it into a more dynamic, responsive, and, ultimately, secure process.
The Importance of Proactive Data Security for Organizational Productivity and Growth
While preventing all potential data breaches is impossible, a proactive approach to data security can significantly mitigate the damage to a company’s reputation and revenue following an incident. To illustrate this point, let’s consider the cost of the data breach suffered by Equifax.
Equifax, one of the largest credit bureaus in the US, suffered a major data breach in 2017, exposing the personal information of 147 million people. This incident resulted in the company losing over $4 billion in market value almost overnight.
Furthermore, aside from the immediate financial losses, the reputational damage was widespread and long-lasting. Once customers lost confidence that their data was secure, they avoided doing business with the company, resulting in even greater losses.
The story could have been different if proactive data security practices had detected the breach earlier. If the company had patched the security vulnerability before it was exploited, it could have prevented billions in losses and preserved its reputation.
The case of the Equifax breach gives us a lot to think about, especially considering the current stance of many companies on data security. According to Cost of a Data Breach Report 2023, globally, the average data breach cost in 2023 was $4.45 million, a 15% increase over 3 years.
Proactive Data Security with Satori
Satori’s Data Security Platform provides a comprehensive and proactive approach to data security. Proactive data security, with its emphasis on prevention, is a vital component of any comprehensive cybersecurity strategy. By implementing solid data access control, posture management, and automation into their security processes, organizations protect their data from potential threats before they cause harm.
To learn more about how Satori can help with proactive data security, book a 30-minute consulting call with one of our experts.



