Healthcare organizations and those dealing with healthcare data are subject to HIPAA compliance requirements. Data and security teams are constantly trying to keep up with regulations that are not only evolving but sometimes vague. One way that data teams have developed to ensure compliance is by controlling access to data based on meeting specific HIPAA requirements.
Data teams can develop automated workflows that ensure users have the requisite HIPAA training before granting them access to the data. This ability means that the organization remains compliant without burdening the data or security teams who need to make sure that all of the employees have met the requirements.
Read about how Satori streamlines HIPAA technical safeguard compliance.
HIPAA’s Privacy Rule
Healthcare organizations and those dealing with healthcare data are subject to HIPAA regulations. As part of HIPAA, covered entities must adhere to the Accountability Principle within the Privacy Rule 45 CFR § 164.530 administrative requirements. This rule requires covered entities and business associates that exchange protected health information (PHI) to comply with HIPAA administrative requirements.
There are several requirements covered in the Privacy Rule but for this use case we focus on the requirements to:
- provide employees with training.
- implement appropriate administrative, physical, and technical safeguards.
These requirements are designed to ensure that employees know how to protect PHI. However, there is significant variability and flexibility to develop and implement procedures to meet these requirements.
While there is no specific guidance on how often or when this training needs to occur. Best practices are holding annual sessions with additional ones as needed. Each covered entity must provide written policies and procedures to implement the rule’s privacy standards and train workforce members. Workforce members who violate the Privacy Rule are subject to sanctions.
One way that has emerged to meet this requirement is to make HIPAA training a requirement for gaining access to data. Since covered organizations must comply with this rule, one option is to implement different masking rules for those employees with access to PHI who have completed HIPAA training versus those who have not completed training.
Locating and Classifying PHI and PII
The first step is to ensure that all sensitive information is discovered and classified. Satori’s continuous discovery of sensitive data means that Satori discovers the location of PHI and PII categories to classify these variables.
Classifying PHI and PII
There is no need to define PHI or PII variables! Satori has a set of predefined PHI and PII categories that track classifications of objects within datastores. Satori also enables data stewards to create custom classification types; meaning, any sensitive data can be classified, tracked and masked/hashed/redacted as part of a data compliance effort.
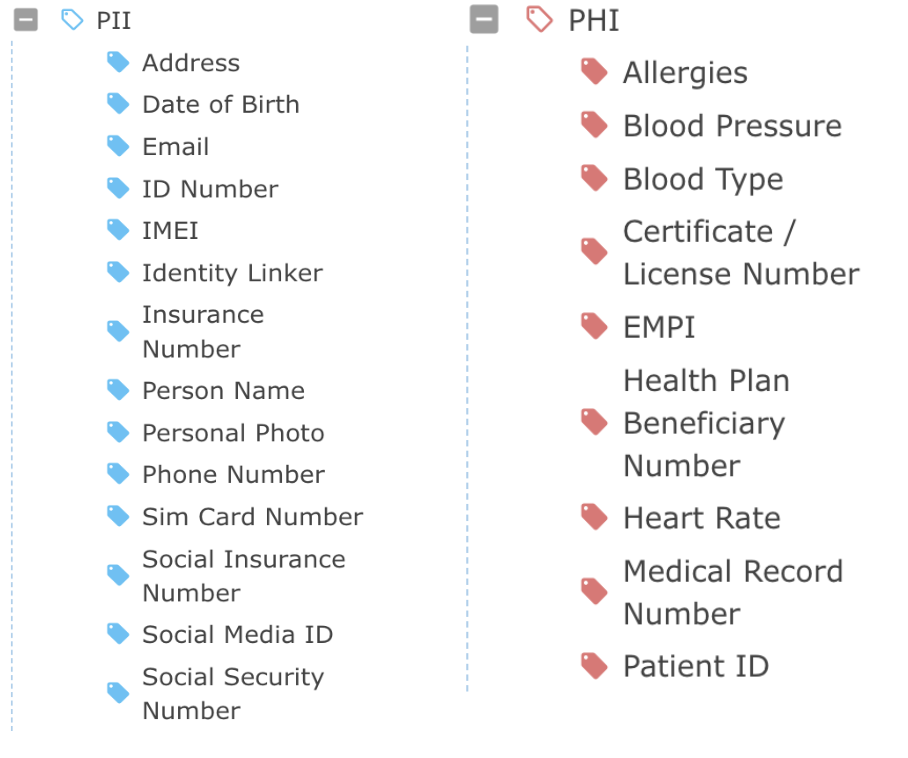
Discovery of PHI and PII
Satori discovers, locates and classifies variables such as PHI or PII, across the diverse data landscape. Including cloud datastores such as AWS Postgres, Azure Synapse, Snowflake and Databricks.
The Satori data inventory capability does not require periodic scanning or database credentials. By analyzing queries and data traversing the Satori platform, the system can generate the data inventory model as well as classify the accessed data.
This approach to data classification alleviates most of the manual toll involved in maintaining an up-to-date data inventory.
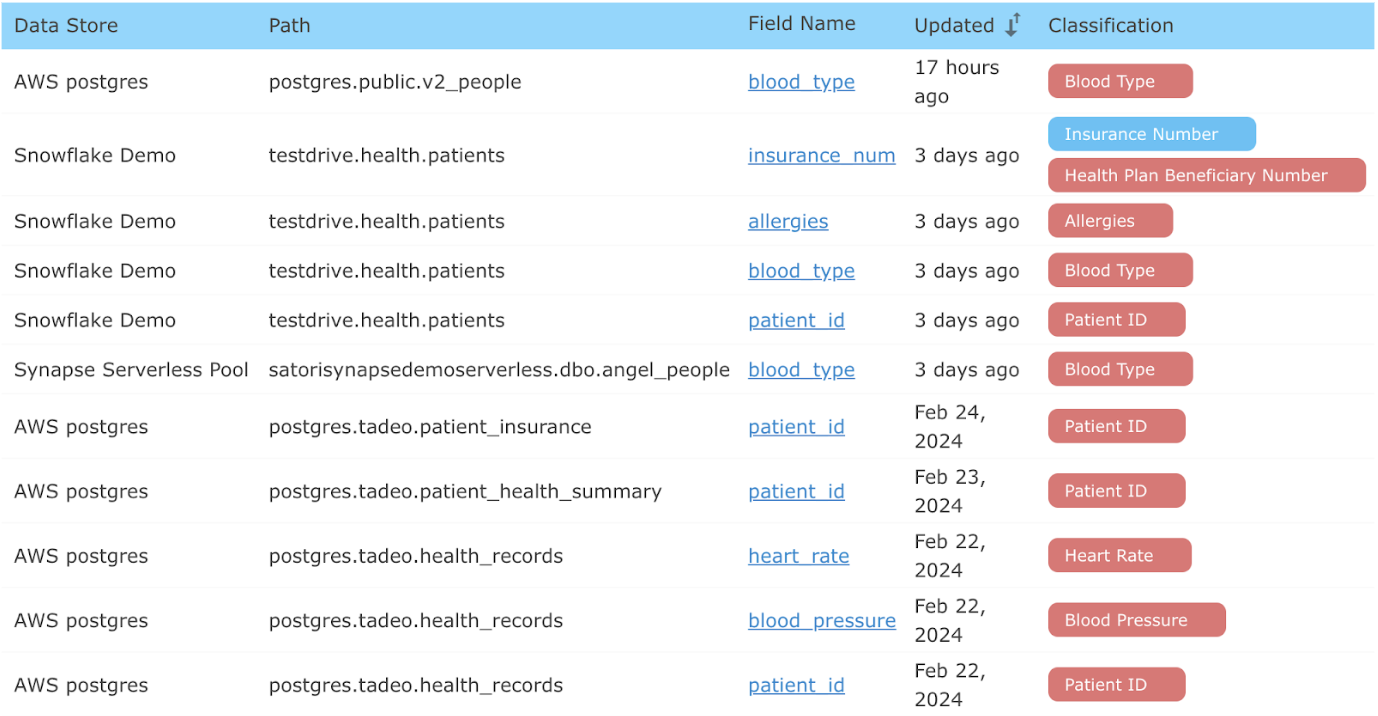
Now that all sensitive, PHI, and PII variables are classified, discovered and tracked. The next step is to set up the masking rules based on whether the user has completed HIPAA training.
Data Access Based on HIPAA Training
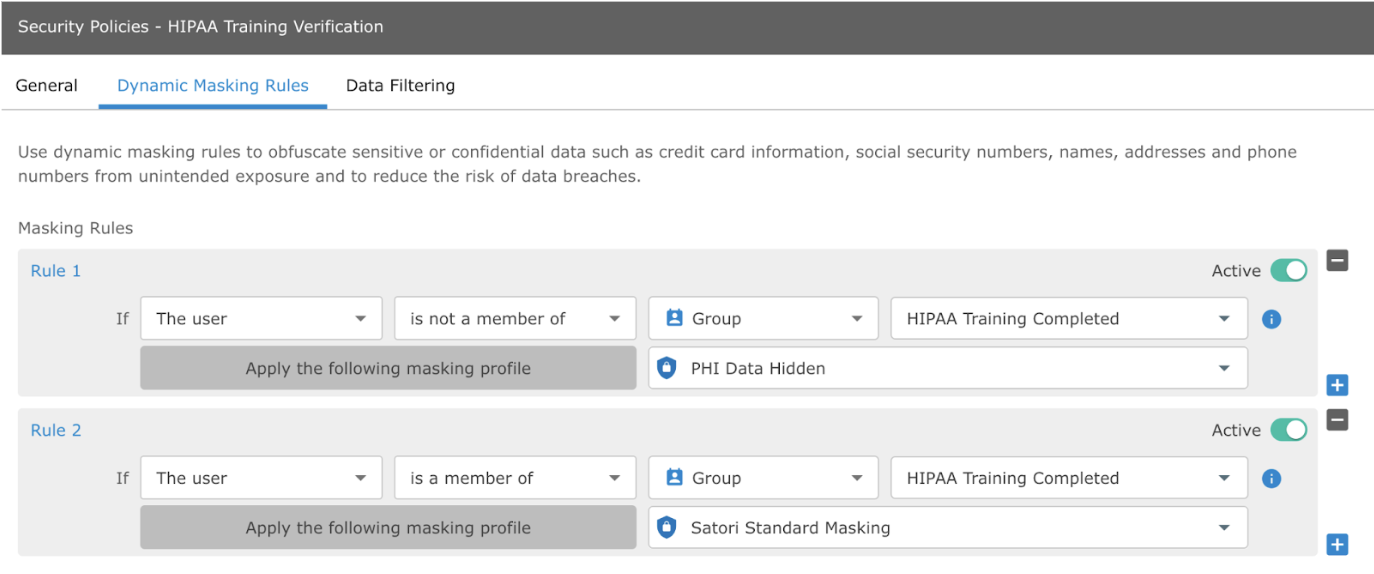
Dynamic masking rules are configured and enforced on data users, based on whether the user has completed HIPAA training. The user is defined as either a member of the Group “HIPAA Training Completed” OR as not a member of the Group “HIPAA Training Completed.”
This group membership can be controlled via Single Sign-On platforms such as Okta, Microsoft Entra ID, or Google Workspaces; or through an API call to the Satori platform to update the “Training Completed” flag for the user.
Based on whether the user is a member of the group determines the masking rule that is applied: either “PHI Data Hidden” or “Satori Standard Masking.”
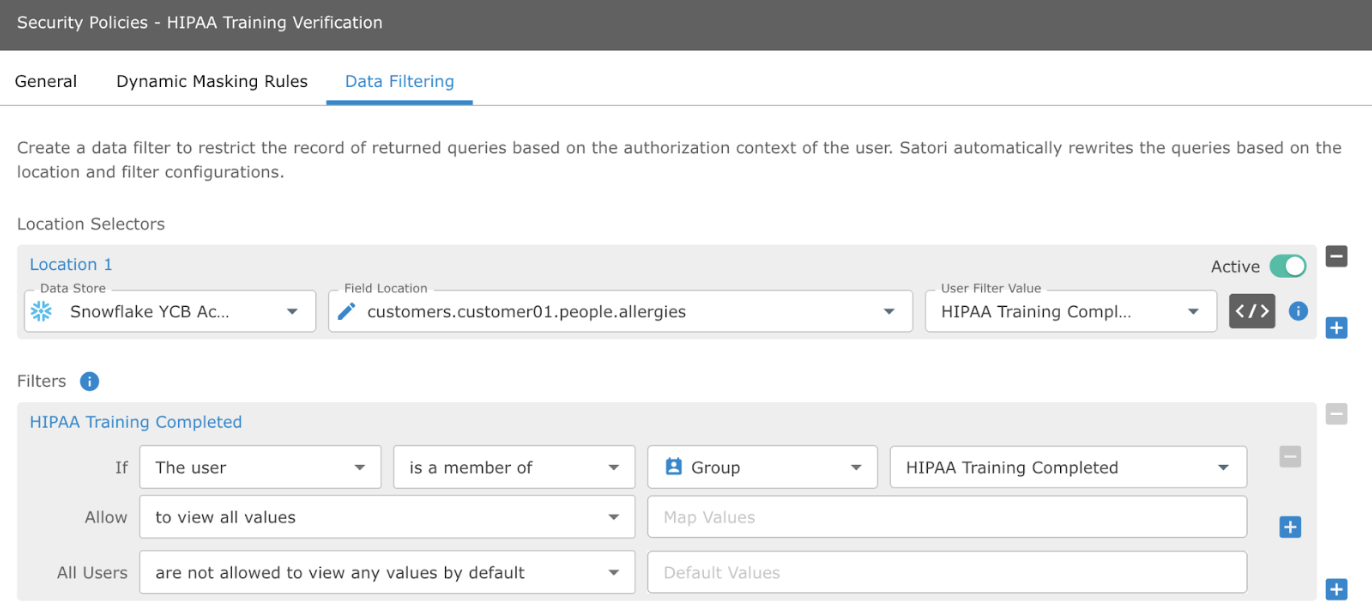
In addition, data teams can apply a corresponding data filtering rule. Completion of HIPAA is a prerequisite for gaining access to PHI data. The data filtering rule redacts data if the user has not completed HIPAA training.
The filtering rule indicates that the default user is not allowed to view any values of PHI data. However, if the user has completed HIPAA training, they can view all values.
In addition to the data and filtering rules, we define the variable masking profiles. These control the action that Satori takes depending on the user’s membership in the group “HIPAA Training Completed.”
Masking Profiles
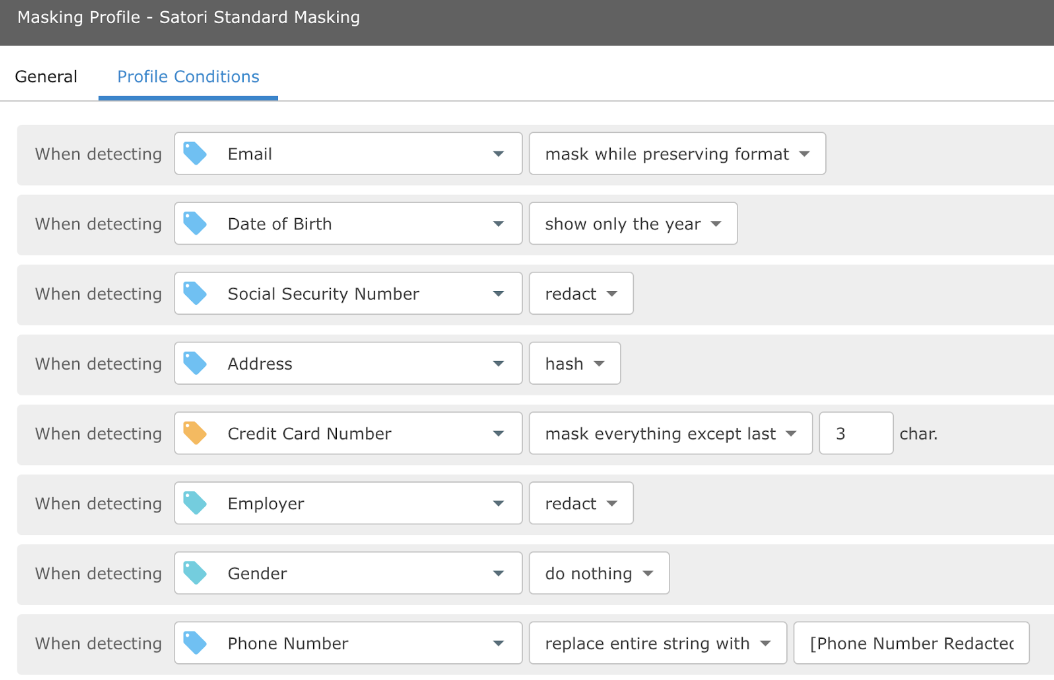
Define the masking profile for PHI and PII variables. The masking rules for “Satori Standard” have the following profile. The masking rules detail the depth and format of the hashing and masking of PHI or PII for the Satori Standard user.
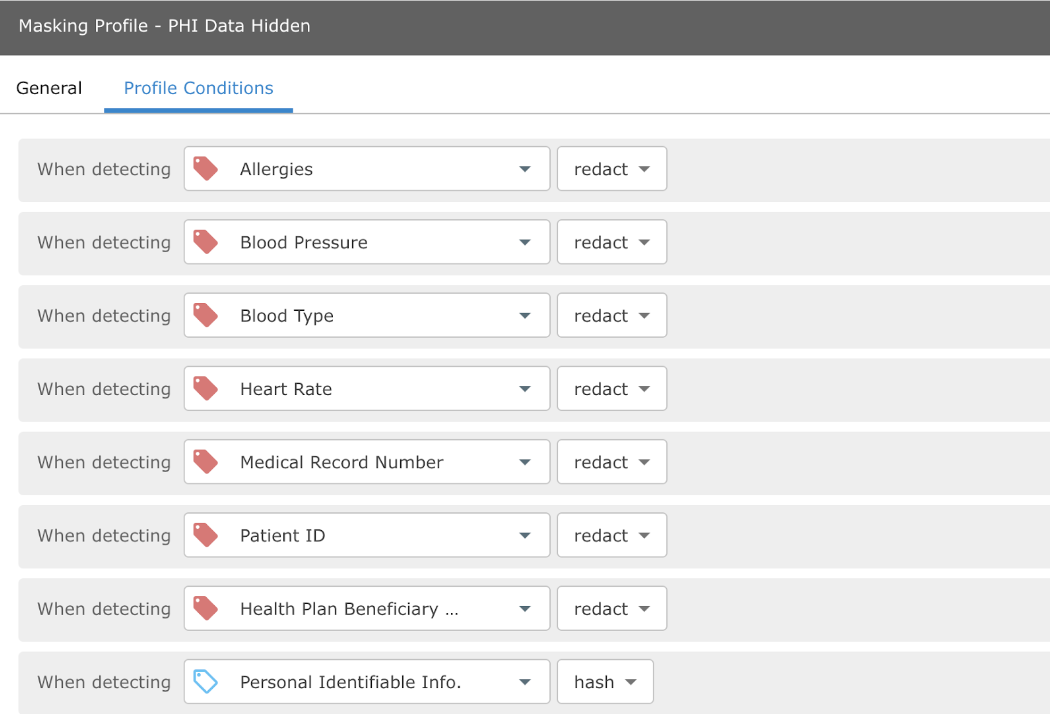
Conversely, the “PHI Hiding” masking profile shows that all PHI is redacted.
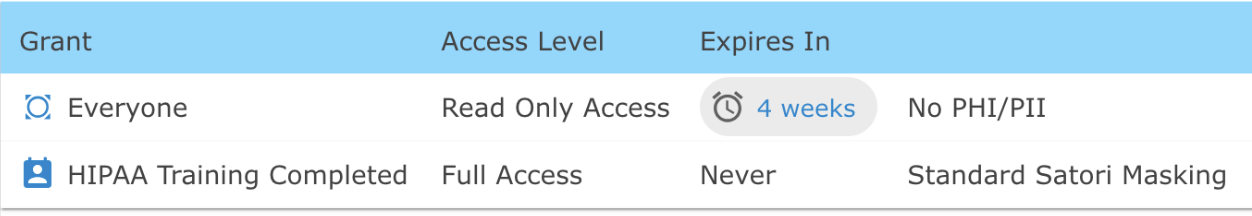
Access Control Policy
The final step is to set up the access control policy for HIPAA protected data. In this example anyone who has passed the HIPAA training gains full access subject to “Standard Satori Masking.” Those employees who have not completed HIPAA training have read only access and are subject to No PHI/PII masking (all data is redacted).
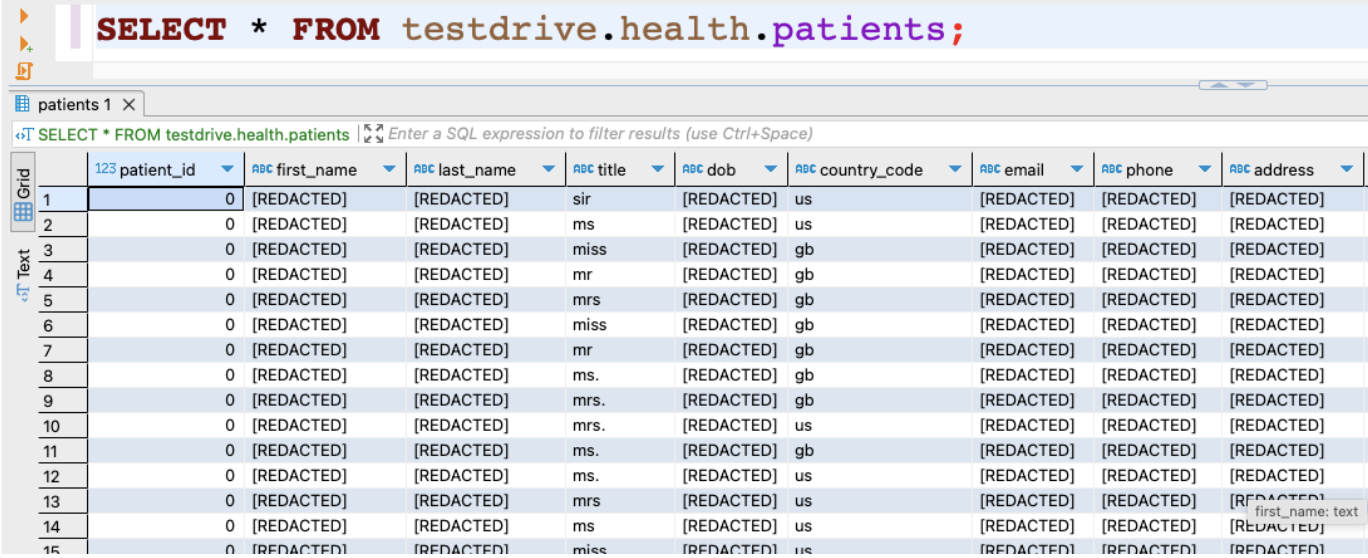
So what does this look like in practice? If the user queries the healthcare data but has NOT passed HIPAA Training the results appear similar to the following:
Conversely, a query result for the same healthcare data for a user who has passed HIPAA training results in the following:
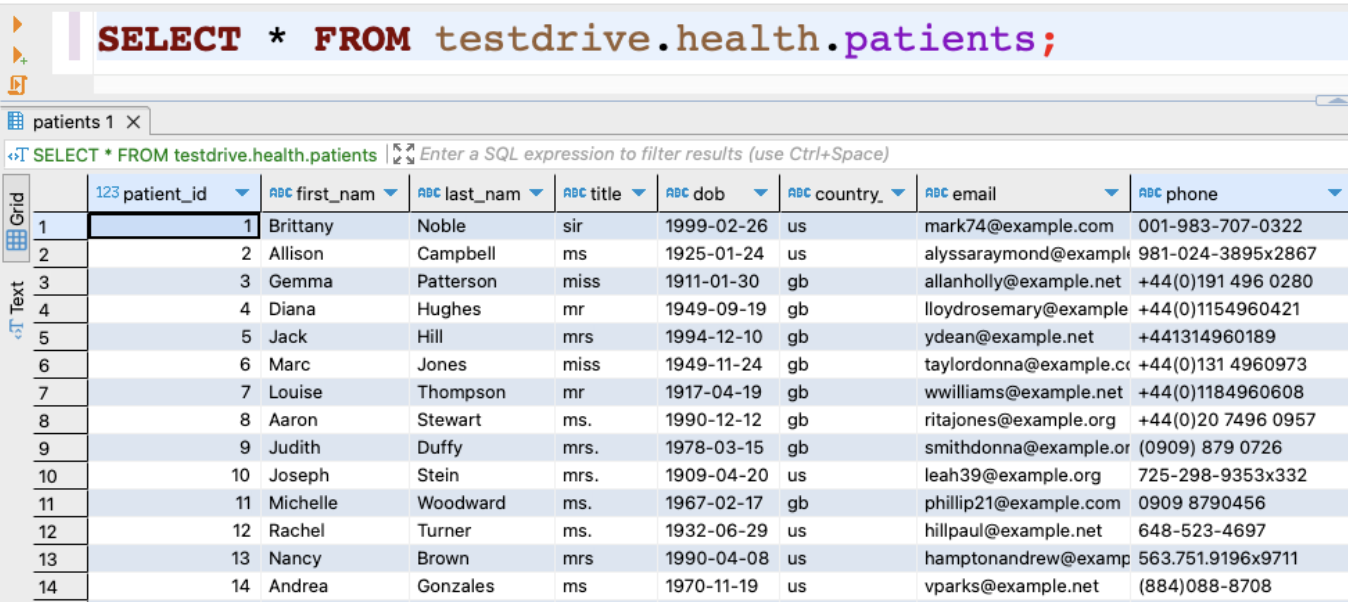
This approach allows the company to control access to data using HIPAA training. This enables the data and security teams to ensure that all users have completed their training to meet the Privacy Rule’s compliance standard.
Auditing Users Access
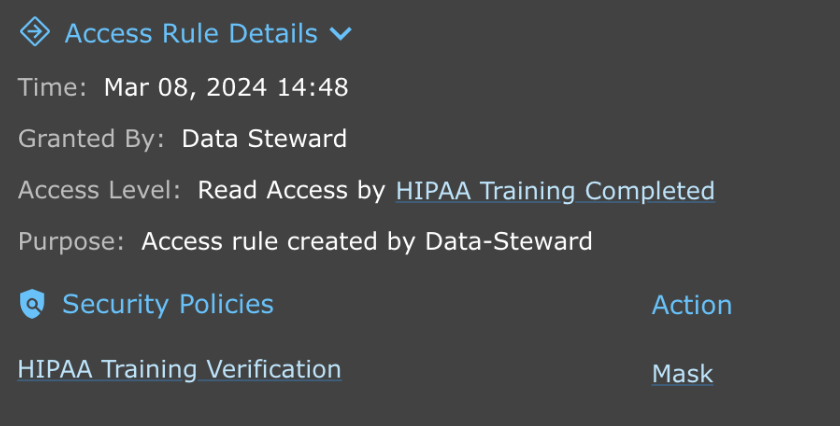
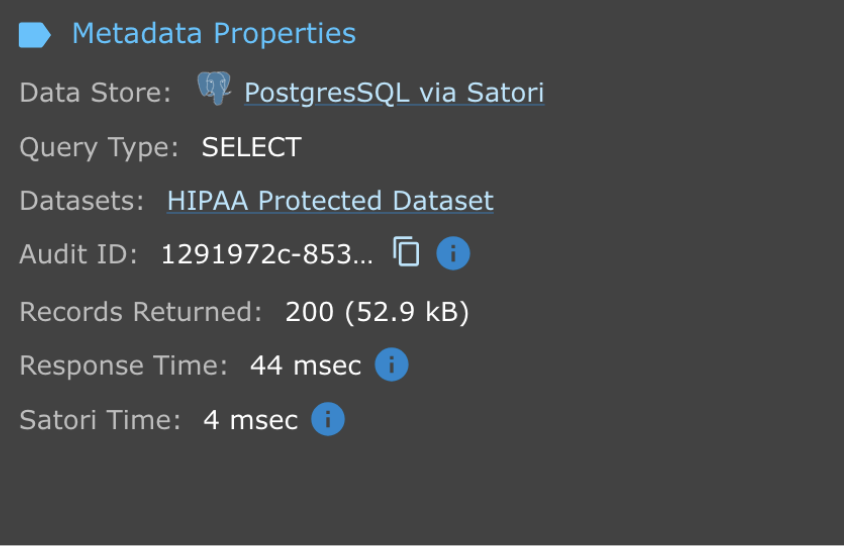
In addition to controlling access to data through HIPAA training. The data teams can also audit the user’s access to data. The audit trail provides information about the user and access rules, including whether the user has completed HIPAA training and the associated metadata.
The visibility and audit trail enables the data and security teams to meet their compliance and audit requirements easily.
Conclusion
Data and security teams are often tasked with controlling access to data. Security teams must ensure that organizations, especially covered entities, meet the administrative procedures outlined in the Privacy Rule. This requires that all workforce employees undergo training and implement the appropriate administrative, physical, and technical safeguards. One way to achieve this is by only enabling access to sensitive PHI and PII data once the employee has passed the requisite HIPAA training.
In this use case, data teams can easily search, discover, and classify sensitive PHI and PII data across diverse data stores. Then after setting up the masking and access rules only users who have completed the training can access sensitive data.
To learn more about how Satori enables access to sensitive data based on HIPAA training set up a demo with one of our experts.




