More From Ben Herzberg
Satori levels up in Snowflake’s Partner Network tier by enabling instant, self-service data access that...
Satori today announced its participation in the Microsoft Security Copilot Partner Private Preview.
Satori sweeps 33 badges in the G2 Fall 2023 reports and is recognized as a...
Explore the hidden privilege creep threat, where the accumulation of access rights puts your data...
Satori's Posture Management provides comprehensive visibility and control over data authorizations to proactively protect sensitive...
Satori has been included in the exclusive Microsoft Pegasus Program and is now available on...
Discusses HIPAA's technical safeguards and the benefits covered organizations can accrue from using Satori to...
Satori provides temporary authentication and secures access to sensitive data on a need-to-know basis at...
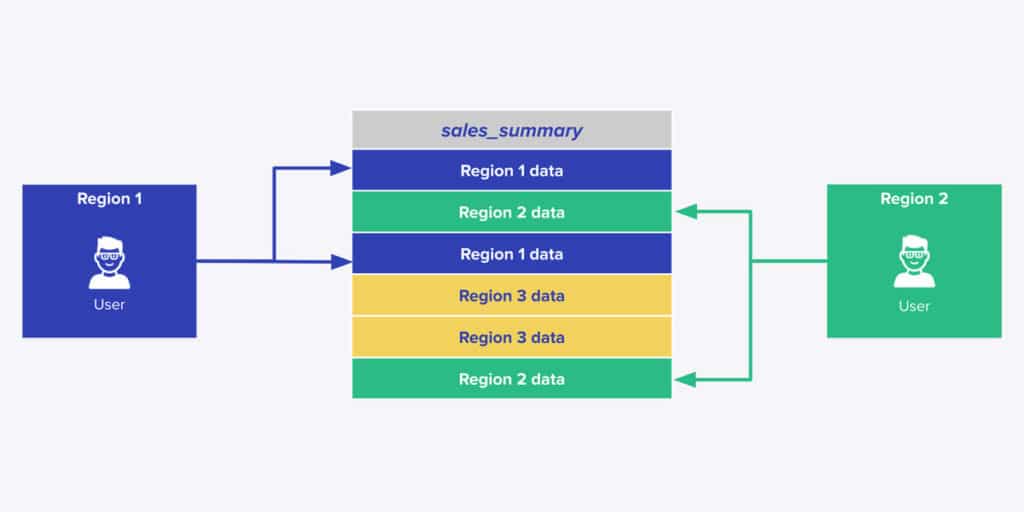
Sharing data is vital to increase organizational productivity, but this raises questions about security risk...
Postgres provides many benefits and has a wide range of useful native security measures, however,...
We explore effective Microsoft SQL user management strategies to keep your users organized, authorized, and...
Native database auditing capabilities, while necessary, in some cases could increase the complexity of an...
Some data store platforms have their own native dynamic masking capabilities. While it may be...
Many organizations are hesitant about data sharing. We explore the problems that prevent and the...
In this report, we analyze and report the results from our survey of 300 industry...
Data ownership is a critical yet often avoided task within organizations. While, individuals shy away...
ABAC is often implemented to overcome the limitations of RBAC, however, ABAC is not without...
The tremendous amount of Healthcare data can generate financial benefits as well as save lives...
The zero trust model requires continuously authenticated, authorized, and validated access to applications and data...
Agile data governance is crucial for organizations using cloud data stores with constantly changing data,...
RBAC is a useful model for access control, however, there are some instances where it...
Data engineering teams can spend a significant portion of their valuable time on cloud data...
Data governance by itself is a complicated procedure that is further compounded when performed in...
Data access control is often described as the Dementor of data engineers due to its...
Data classification projects are a dark cloud for data teams, often appearing randomly and redirecting...
Data security is critical, however, this task often defaults to already overwhelmed data engineering teams...
Data masking is essential when working with sensitive data. However, there are a number of...
Stakeholders including data consumers are ultimately people. Having an annoying work environment reduces productivity and...
Uncontrolled employee access to production environments is an operational challenge, because while access is necessary...
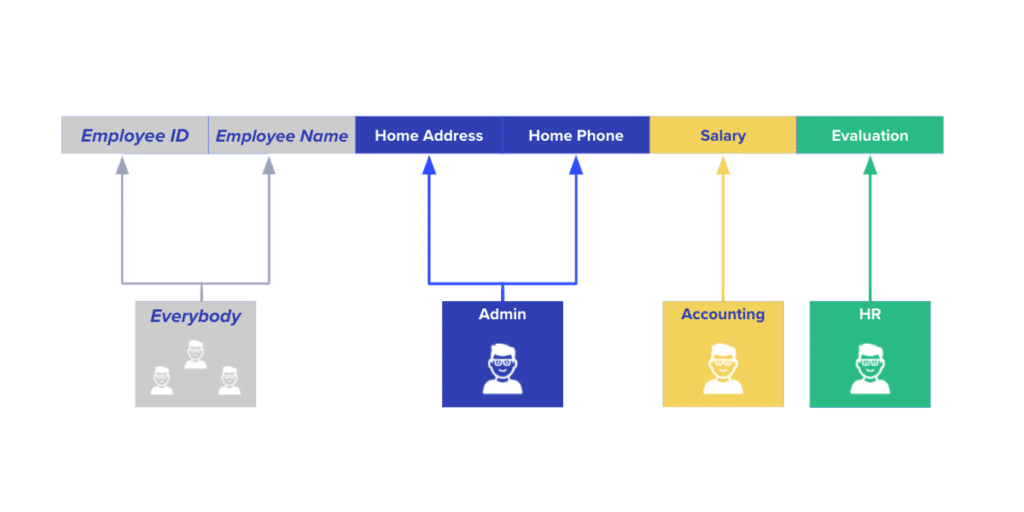
Classifying data as "need-to-know" is important for securing sensitive data. In this post we discuss...
Managing security and access policies from a consolidated platform simplifies processes and increases visibility and...
One of the common pain points data teams experience in authorizing users to access data...
Making life more simple for our customers not only means striving to deliver the best...
One of the most commonly used productivity tools is Slack, and the ability to control...
For years, we have been following our mission of enabling companies to deliver quicker data-driven...
Meeting data localization requirements can be challenging; this post explains how to simplify them with...
Satori and CockroachDB are announcing a partnership that will enable existing and new Satori and...
We’re announcing MySQL support in Satori to help companies secure their data access for MySQL...
A proxy server can be a forward proxy where the client directs traffic through a...
Before they can access data, users must get authenticated and authorized. In this regard, access...
In this article, I will give an overview of data access orchestration (not to be...
Some of the most common questions we, Satorians, encounter are about the many Satori deployment...
The more data a company collects and stores, the more likely that data can turn...
We all like having our cake and eating it too. In this article, we will...
This article will discuss the distinction between tokenization and encryption and their inverses: decryption and...
Data dictionaries, inventories, and catalogs are terms often used interchangeably. While they are all critical...
A lot of thought goes into how to help potential customers try out your product....
For the last few years, we at Satori have been a bit obsessed with Snowflake....
Access management has evolved to incorporate need-to-share authorizations in addition to need-to-know information. The authorization...
The future of data democratization lies in the hands of your end-users. They are already...
One account is not enough. In many cases, organizations using Snowflake use multiple accounts rather...
As the saying goes, “data is the new oil,” as it is quickly becoming an...
Today, as part of Snowflake’s global Snowday event, we are excited to announce our participation...
There is no such thing as a one-size-fits-all data governance framework that works for all...
Satori augments your Collibra data governance capabilities and creates a synergy for better DataSecOps across...
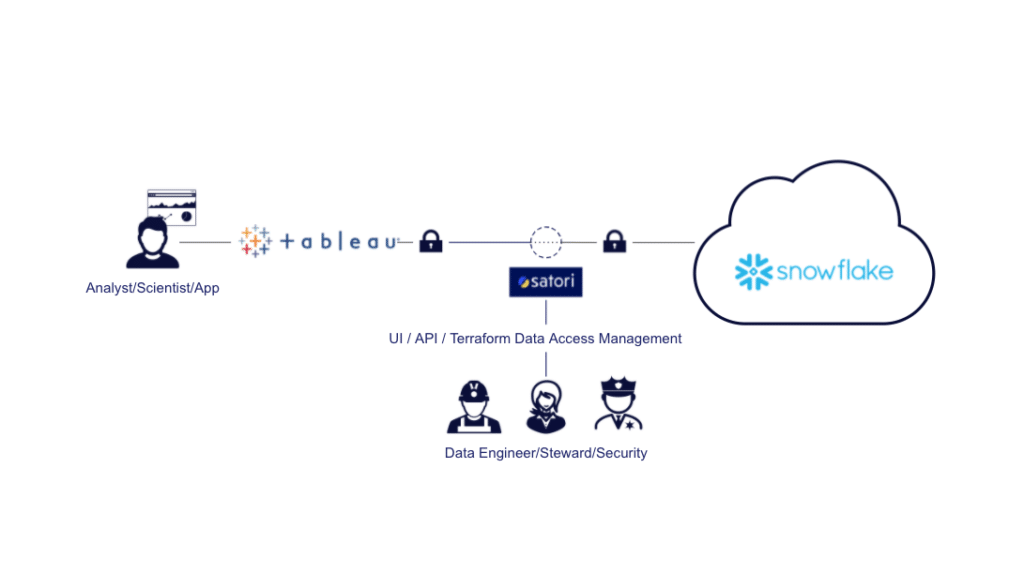
Many organizations are using Tableau to empower their BI activities for reporting and analytics. These...
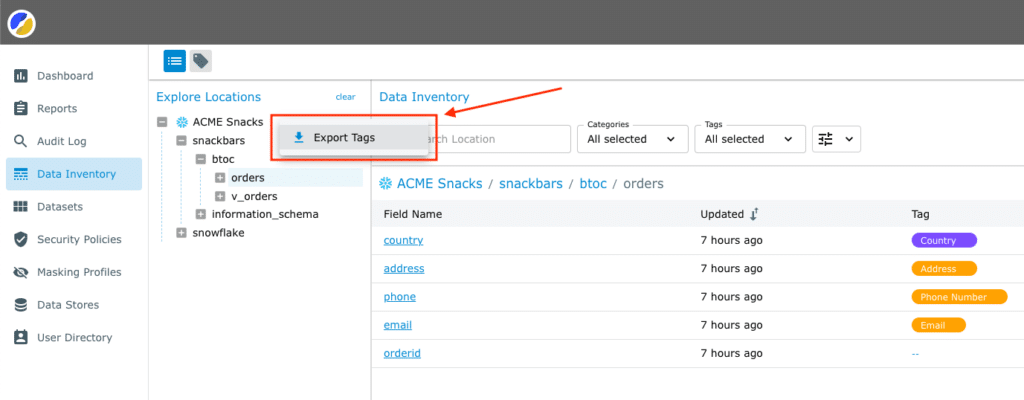
In a previous post, we introduced you to our data classification capabilities. As a recap,...
Machine learning has been commoditized in the last decade or so, and I love it....
When data engineers and other professionals experience Satori for the first time, one aspect they...
Tableau is one of the most widely used BI tools which provides a wealth of...
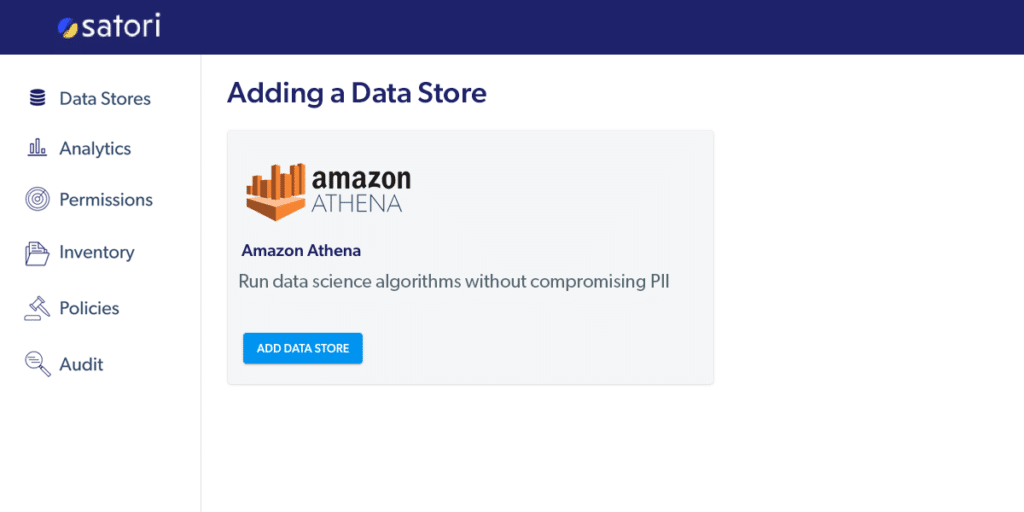
A few years ago, when I first began using Athena, it was a magical and...
I love hiking as well as outdoor navigation. What I find especially useful for these...
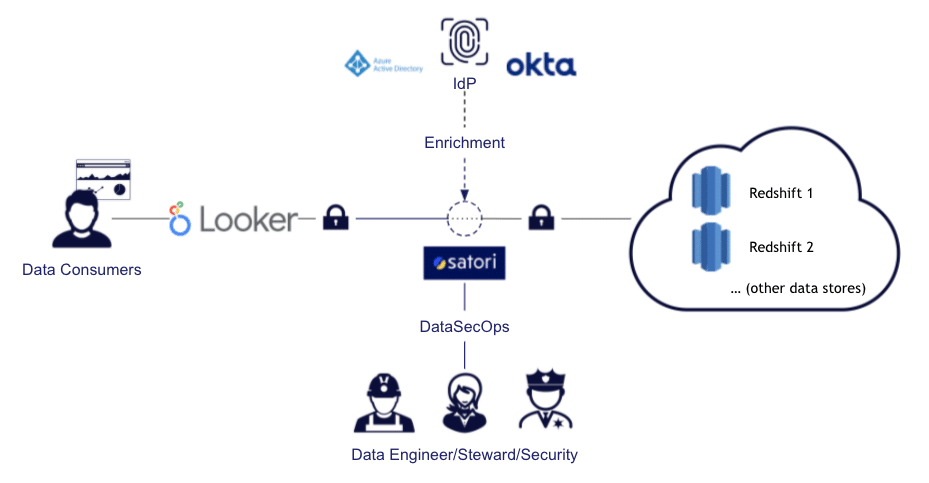
I’m guessing there is no need to introduce you to Amazon Redshift or Google Looker,...
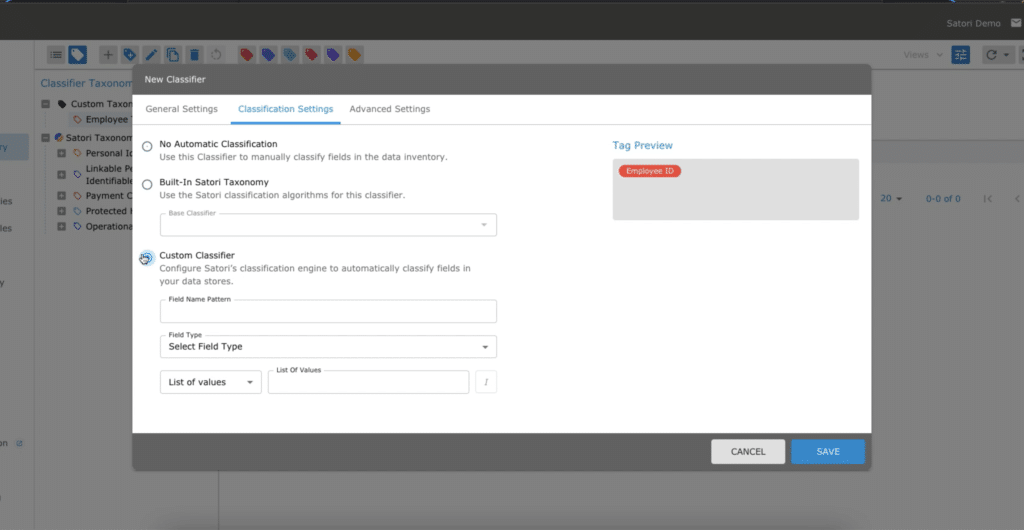
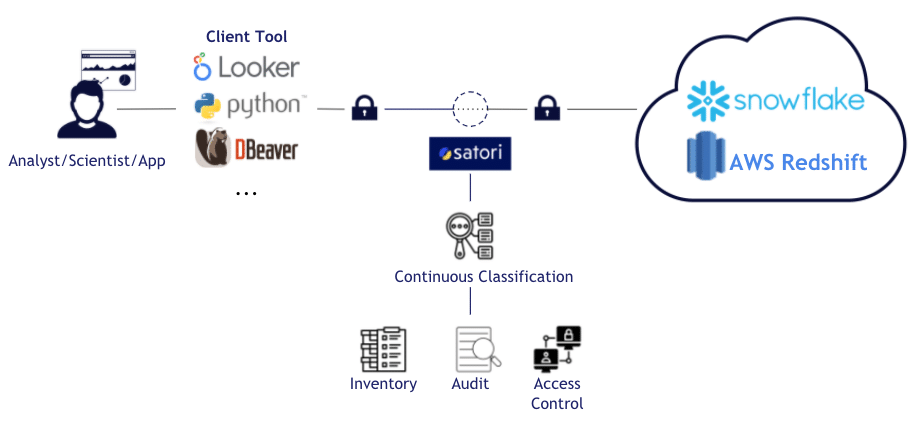
In this article, I will discuss how people perform data classification using Satori and explain...
In the first part of this article, we discussed the many reasons why you should...
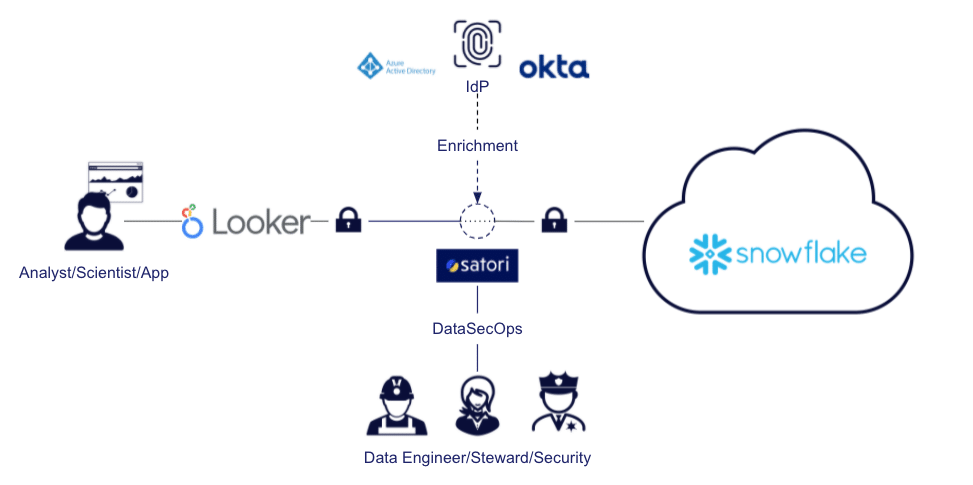
In this post, we will discuss the DataSecOps advantages that Looker users over Snowflake enjoy...
Note: this is part 1 of the guide, in part 2 we discuss the questions...
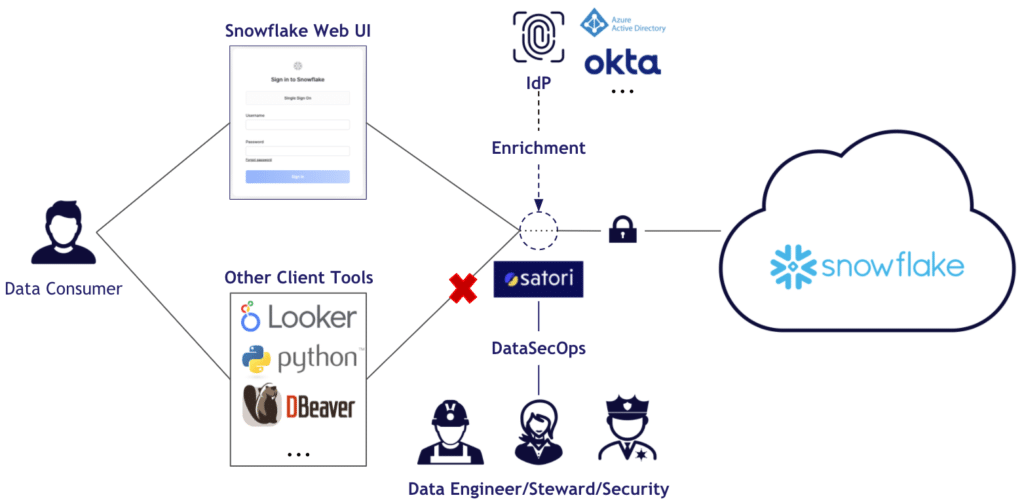
Before we drill down to the “why” and “how” of limiting client tool access in...
Amazon Redshift allows companies to analyze large amounts of data, whether the data is stored...
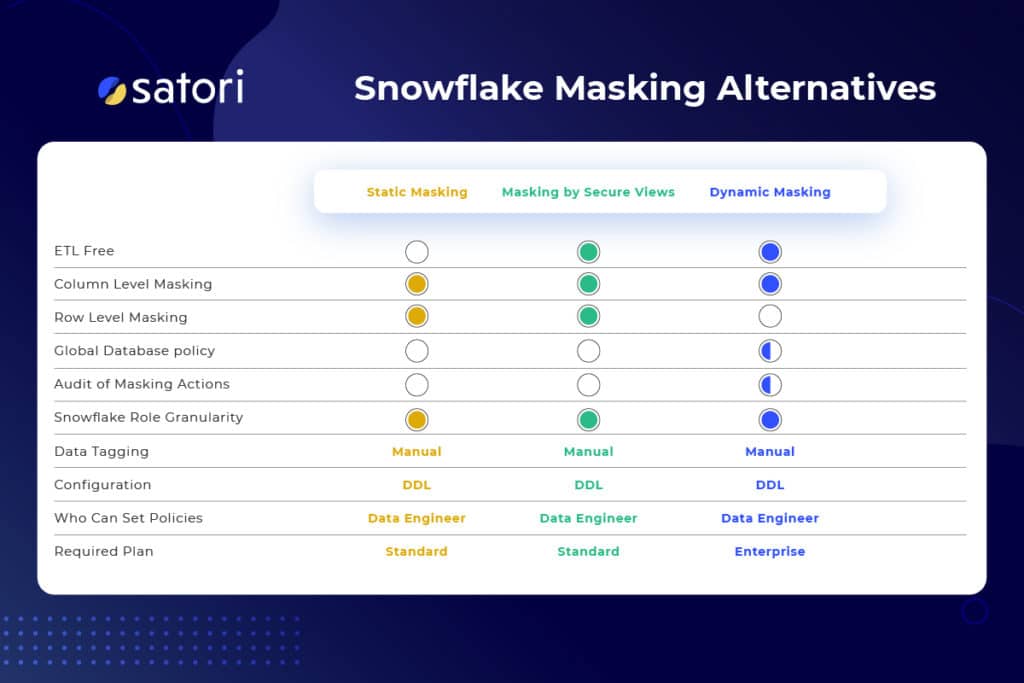
Let’s start with good news – if you are using Snowflake and want a simple...
This article is also published as a chapter in our Snowflake Security guide, covering many...
History repeats itself. The transition of applications to the cloud and the development of software...
2022-12-01 If you’d like to view the entire guide of AWS Redshift Security topics, visit...
Every year, the cybersecurity industry has its biggest conference, the RSA conference in San Francisco...
Snowflake’s data access modeling is different from many other databases and data warehouses. It’s funny...
Creating and maintaining a data inventory is an important part of a comprehensive data management...
Data masking is the act of transforming parts of data to maintain its anonymity. There...
Being optimally focused is the key that helps you spend your resources better. When your...
There are moments when architecting data where you need to make decisions that will have...
The Snowflake Data Cloud helps organizations quickly transition from having a lot of data to...
In today’s ever-evolving digital age, data masking is one of the most essential features of...
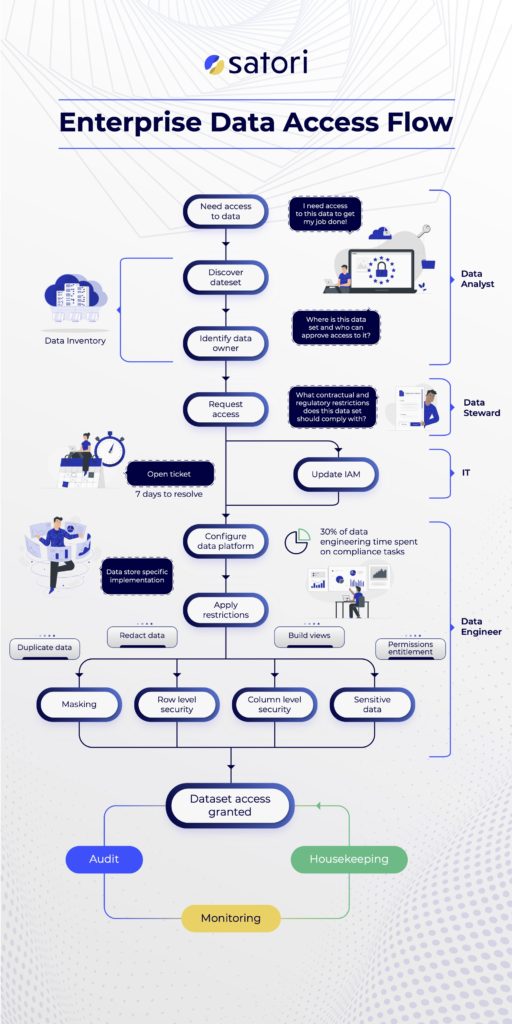
Let’s understand the chain of events that leads to data access. For example, imagine you...
A few days ago, I wrote about some of the complexities of managing Snowflake roles...
RBAC, or Role-Based Access Controls, are foundational tenets of good data governance and key to...
Benchmarking Snowflake DB with TPC-H, including full queries and source code.
Data migration is not fun. I’ve been there, done that, and I did not like...
How to get better access control & security for your data lake using Satori along...
Column-level security in Satori for Snowflake, simplifies data and security teams life so they can...
How to implement Snowflake row-level access control, a step-by-step guide, with secure views or by...
Native DB access logs are useful, but using Satori to analyze data access logs helps...
Data engineers are often conflicted between engineering teams, security and privacy.
I recently published a lengthy diatribe about the problem of over-permissive access to data, the...
Meeting GDPR requirements is important, not only for EU companies but also for any companies...
Update – January 12th 2021: Following Snowflake’s preview addition of self-service account creation using the...
In the spirit of our Snowflake DB security and AWS Redshift security guides, we’ve created...
I need to get something off my chest. It’s time for our beloved infosec community...
This is part of our complete Amazon Redshift Guide.
If you’d like to read this guide, along with additional guides to specific topics in...
Implementing security products, services and solutions in enterprises is intrinsically difficult, especially when coordinating several...
“Laying out data infrastructure for a new product and big-data research is no small task....
This week, the Washington senate approved the Washington Privacy Act (WPA) to advance data privacy...
As the world undergoes a data revolution, the ways we generate, store, access, use and...
Register Here
The latest posts delivered to your inbox